COMP 3511: Lecture 4
Date:
Reviewed:
Topic / Chapter:
summary
❓Questions
Notes
Cloud Computing
-
Cloud computing & virtualization
- delivers: computing, storage, or apps as a service over a network
- logical extension of virtualization: combination of virtualization & communication
- Amazon EC2: w/ millions of servers, and tens of millions of VMs
- petabytes of storage available across the Internet
- payment: based on usage
- Amazon EC2: w/ millions of servers, and tens of millions of VMs
-
Cloud types
- public cloud: available vis Internet to anyone willing to pay
- private: run by company for internal use
- hybrid cloud: includes both public & private components
- software as a service (SaaS): provides one / more apps via Internet (web based application)
- no installation required
- platform as a service (PaaS): provides SW stack ready for application via Internet
- e.g. database server, Google Apps Engine, Heroku
- infrastructure as a service (IaaS): provides servers / storage over Internet
- e.g. VM instances, cloud bucket
- other services: also appearing
- e.g. machine learning as a service (MaaS)
Free & Open Source
-
Free and open source OS
- OS: often made available in source code, rather than just binary
- yet: MS Windows: closed source
- idea: started by Free Software Foundation (FSF) w/ "copyleft" GNU Public License (GPL)
- free software != open-source software
- free software: licensed to allow no-cost use, redistribution, modification
- in addition to public source
- open source: not necessarily w/ such license
- popular examples:
- GNU / Linux
- FreeBSD UNIX (and core of MAx OS X - Darwin)
- Solaris
- open source code: arguable more secure
- more programmers to contribute & check
- a better learning tool for us
- OS: often made available in source code, rather than just binary
OS Services
-
OS services
- OS: provides environment for execution of programs
- and other services to programs & users
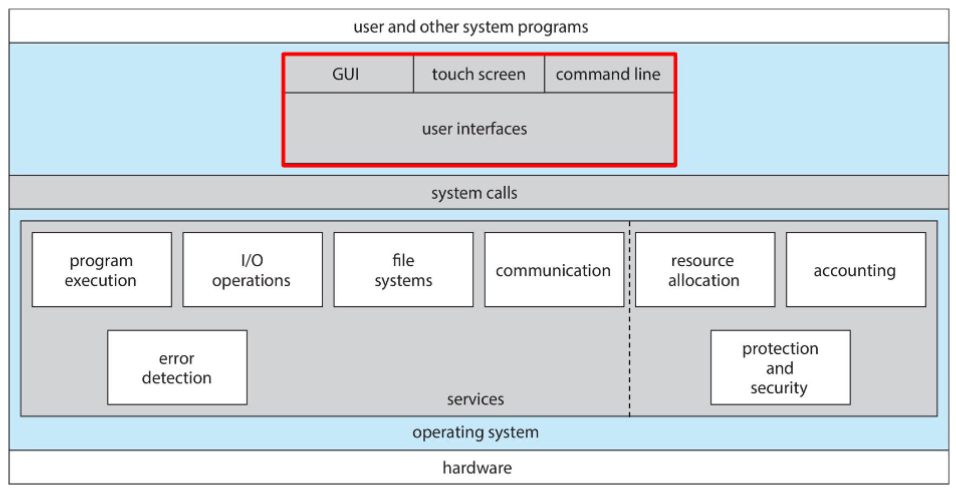
- set of OS services (OS functions) helpful to user
- user interface: almost all OS has a user interface (UI)
- command line (CLU), graphics (GUI), touch-screen
- program execution: system: must be able to load program into memory
- and run the program & end execution
- either normally or abnormally (= error)
- and run the program & end execution
- IO operations: running program: may require IO
- might involve: files / IO device
- ⭐ file-system manipulation: programs: need to read & write files and directories
- in additions to: search, create, and delete
- and further: listing file information / permission management
- communications: processes: may exchange information (on same computer, or over a network)
- via: shared memory or through message passing (packets: moved by the OS)
- error detections: OS needs to be constantly aware of possible errors
- may occur in CPU, memory, IO devices, user programs
- for each error type: OS must take appropriate actions
- to ensure: correct & consistent computing
- debugging facilities: can greatly enhance the user's and programmer's abilities
- to efficiently use the system
- user interface: almost all OS has a user interface (UI)
- other set of OS services: ensures efficient operation of system (via resource sharing)
- resource allocation: within multiple concurrent users & jobs
- resources: must be allocate to each of them
- e.g. CPU cycles, memory, file storage, IO devices
- resources: must be allocate to each of them
- logging: keep track of: which users use how much
- and what kinds of computer resources
- protection, security: owners of information stored in multi-user / networked system: might want control on information use
- e.g. permission control
- concurrent processes: should not interfere with each other
- protection: involving ensuring that all accesses to system resources: controlled
- security of the system from outsiders: requires user authentication
- extends to: defending external IO devices from invalid access attempts
- resource allocation: within multiple concurrent users & jobs
- OS: provides environment for execution of programs
-
User OS interface: CLI
- generally: three approaches for UI exists
- CLI / command interpreter - directly enters commands to OS
- GUI / touch screen: allows user to interface w/ the OS
- CLI: allows direct command entry
- sometimes: implemented in kernel
- sometimes by system programs
- sometimes: multiple flavors implemented: shells in Unix / Linux
- primary functionality of shell:
- fetching command from user
- interpreting it
- executing it
- UNIX and Linux systems: provide different version of shells
- e.g. C shell, Bourne-Again, Korn, et.
- sometimes: implemented in kernel
- generally: three approaches for UI exists
-
User OS interface: GUI
- user-friendly desktop metaphor interface
- usually: mouse, keyboard, and monitor
- icons representing files, programs, directories, system functions, etc.
- various mouse buttons over objects: cause various actions
- e.g. provide information, execute function, open directory, etc.
- invented at: Xerox PARC earlier 1970s (near Stanford)
- first wide use: in Apple Macintosh (1984)
- many systems now: provide both CLI and GUI interfaces
- MS Windows: using GUI w/ CLI command shell
- Apple Max OS X: Aqua GUI interface
- w/ UNIX kernel underneath, as well as shells
- Unix and Linux: w/ CLI and optional GUI interfaces (KDE, GNOME)
- user-friendly desktop metaphor interface
-
User OS interface: touchscreen
- touch screen requires: new interfaces
- mouse: not feasible / desired
- actions & selection: based on gestures (no mouse move)
- virtual (on-screen) keyboard for text
- voice command: iPhone's Siri, etc.
- touch screen requires: new interfaces
Syscall
-
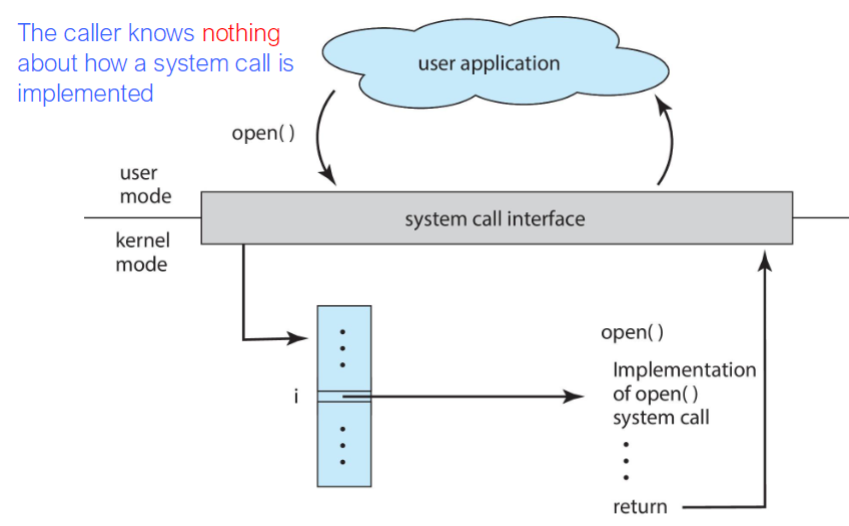
Syscall
- system call: programming interface to the services provided by the OS
- syscall: generally available as functions, written in a high-level language (C/C++)
- certain low-level tasks: written in assembly languages (accessing hardware)
- e.g.:
cp in.txt out.txtinvolves multiple syscall- input file name, accept input, open input file, create out file, etc.
-
API
- application program interface (API): specifying a set of functions, available for app programmers to use
- including: parameters passed to functions
- and expected return values
- including: parameters passed to functions
- function making up API: typically invoke actual syscalls, on behalf of programmer
- programmer: access APIs via library provided by the OS
- in UNIX / Linux:
libcfor C programs
- in UNIX / Linux:
- three most common APIs:
- Win32 API for Windows systems
- POSIX API for POSIX-based systems (UNIX, Linux, and Mac OS X)
- Java API for JVM
- standard API example
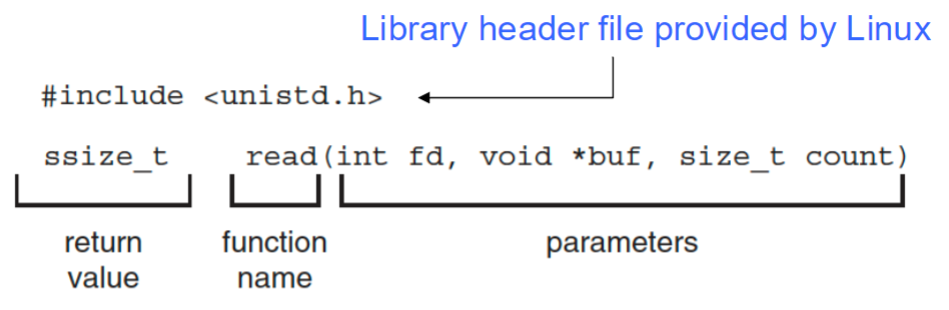
- parameters
int fd: file descriptor to be readvoid *buf: buffer the data will be read intosize_t count: maximum number of bytes to be read: into the buffer
- return value
0: indicating end of file-1: indicating error
- advantages: why use API over syscall?
- program portability: programmer w/ API: expect program to run on any system supporting same API
- syscall implementation: might vary from machine to machine
- abstraction: hiding complex details of the syscall from users
- actual syscall: often more details / difficult to work with
- caller of API: doesn't need to know implementation of syscall
- caller: simply obey API format / understand what does API do
- program portability: programmer w/ API: expect program to run on any system supporting same API
- application program interface (API): specifying a set of functions, available for app programmers to use
-
Syscall implementation
- for most programming languages: run-time environment (RTE) provides syscall interface
- serving as link to syscalls, made available by OS
- RTE: set of functions built into libraries
- each syscall: associated w/ identity number
- syscall interface: maintains a table indexed according to these numbers
- syscall interface: functions
- intercept: function calls in API
- invoke: necessary syscall within OS
- return: status of syscall / return values if any
- API-syscall-OS relationship
- for most programming languages: run-time environment (RTE) provides syscall interface
-
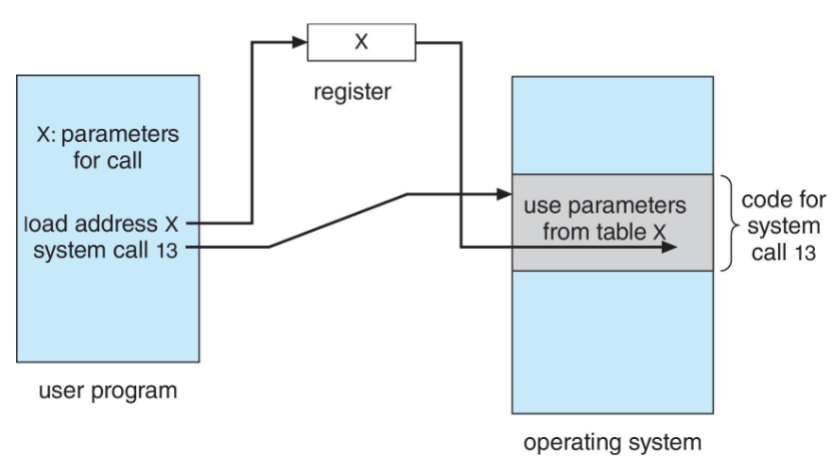
Syscall parameter passing
- often: more info than just syscall identity is needed
- exact type / amount of information: vary for OS / call
- 👨🏫 although we will spend some time on a syscall without parameter (
fork())
- three general methods used to pass parameters from user programs to OS
- simplest: pass parameters in registers
- block method: parameters stored in block / table / memory
- and address of block: passed as a parameter in a register
- stack method: parameters placed / pushed onto stack by the program
- popped off the stack by the OS
- block & stack: no limitation on number / length of parameters!
- parameter passing: via table
- often: more info than just syscall identity is needed
-
Types of syscalls
- process control
- create / terminate process
- end, abort
- load, execute
- get / set process attributes
- wait for time
- wait even, signal event
- allocate / free memory
- dump memory if error
- debugger for determining bugs, single step execution
- locks for managing access to shared data between processes
- file management
- create / delete file
- open / close file
- read, write, reposition
- get & set file attributes
- device management
- request / release device
- read, write, reposition
- get / set device attributes
- logically attach / detach devices
- information maintenance
- get & set time / data
- get & set system data
- get & set process, file, device attributes
- communications
- create, delete communication connection
- send, receive messages: to host name / process name
- if message parsing model
- shared memory model: create & gain access to memory regions
- transfer status information
- attach & detach remote devices
- protection
- control access to resources / get and set permissions
- allow / deny user access
- process control
-
Examples
task Windows Unix process control CreateProcess()fork()ExitProcess()exit()WaitForSingleObject()wait()file management CreateFile()open()ReadFile()read()WriteFile()write()CloseHandle()close()device management SetConsoleMode()ioctl()ReadConsole()read()WriteConsole()write()information maintenance GetCurrentProcessID()getpid()SetTimer()alarm()Sleep()sleep()communications CreatePipe()pipe()CreateFileMapping()shm_open()MapViewOfFile()mmap()protection SetFileSecurity()chmod()InitializeSecurityDescriptor()umask()SetSecurityDescriptorGroup()chown()- standard C library example
- program invoking
printf()library call- leads to
write()syscall, etc. 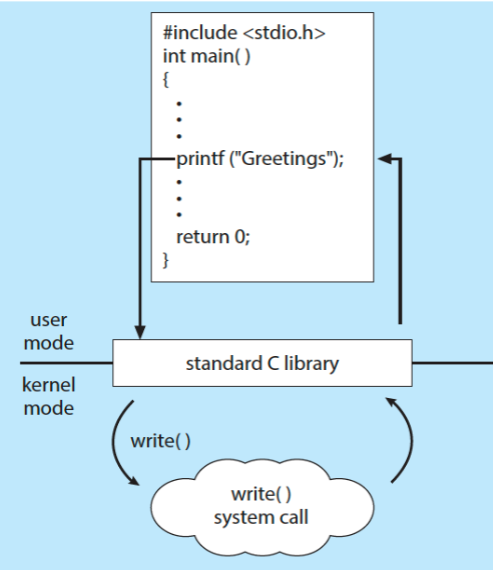
- leads to
- program invoking
- standard C library example
System Programs
-
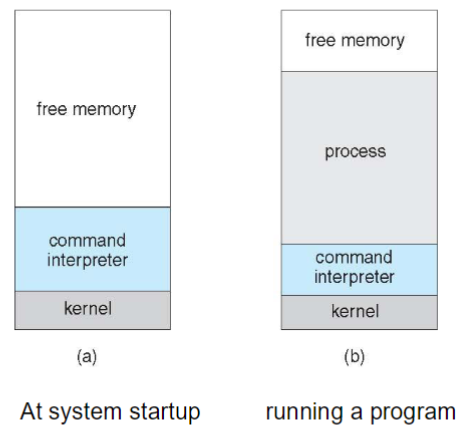
MS-DOS example
- characteristics
- single tasking
shellinvoked when system booted- simple to run a program
- no process created
- single memory space
- loads program into memory
- overwriting all: but the kernel
- program exit =>
shellreloaded
- characteristics
-
System programs
- another aspect of modern computer system: collection of system services
- system services: provide convenient environment for program development / execution
- aka system programs / utilities
- some: simply user interface to syscalls
- others: considerably more complex
- view of OS seen by most users: defined by application & system programs
- not the actual syscalls
- e.g. GUI featuring mouse-and-windows interface vs. UNIX shell
- same set of system calls
- yet, syscalls appear very differently & act in different way (from user)
-
List of system programs
- file management
- create, delete, copy, rename, print, dump, list
- and generally manipulate files & directories
- status information
- some: ask system for data, time, amount of available memory, disk space, number of users, etc.
- others: provide detailed performance, logging, debugging information
- file modification
- text editors to create & modify files
- special commands to search file contents / perform transformation of the text
- program-language support
- compilers, assemblers, debuggers, and interpreters
- for common programming languages (C, C++, Java, Python)
- often provided
- compilers, assemblers, debuggers, and interpreters
- program loading & execution
- absolute loaders, relocatable loaders, linkage editors, overlay-loaders, debugging systems
- for higher-level and machine language
- absolute loaders, relocatable loaders, linkage editors, overlay-loaders, debugging systems
- communications: providing mechanism for creating virtual connections
- among processes, users, and computer systems
- allowing users to:
- send messages to one another's screens
- browse web pages
- send electronic-mail messages
- log in remotely
- transfer files from one machine to another
- background services
- launch at boot time
- some: terminate after completing task
- some: continue to run until system terminates
- aka: services, subsystems, daemons
- provide: facilities like disk checking, process scheduling, error logging
- launch at boot time
- application programs
- not part of the OS
- launched by command line, mouse click, finger poke, etc.
- examples: web browsers, word processors, text formatters, spreadsheet, DB systems, games ...
- file management
-
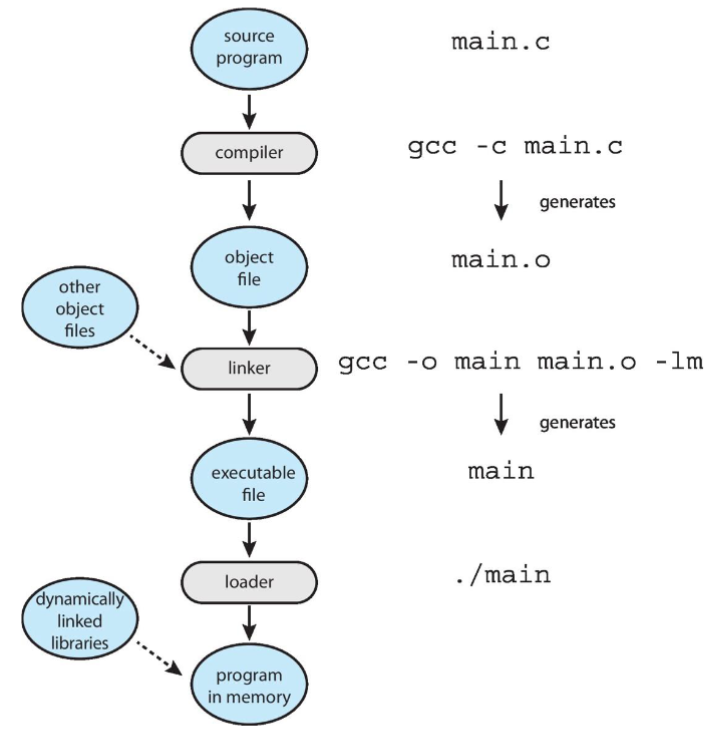
Linkers and loaders
- source codes: compiled into object files
- designed to be loaded into any physical memory location
- relocatable object files
- linker: combines object files into a single binary executable file
- programs: reside on secondary storage as binary executable
- must be brought into memory by loader to be executed
- relocation: assigns final addresses to program parts
- adjusts code & data in program to match those addresses
- modern general purpose OS: don't link libraries into executables statically
- instead: using dynamically linked libraries (aka DLLs in Windows)
- loaded when needed, and shared by all programs using the same version of that library
- loaded only once!
- loaded when needed, and shared by all programs using the same version of that library
- object files / executable files: often w/ standard formats
- machine codes, symbolic tables
- thus: OS knows how to load & start them
- instead: using dynamically linked libraries (aka DLLs in Windows)
- role of the linker and loader
- source codes: compiled into object files
Operating System Design and Implementation
-
Protection
- protection: internal problem
- security: considering both the system & surrounding environment of is
- OS: must protect itself from user programs
Reliability: compromising the OS: generally causes it to crashSecurity: limit the scope of what processes can doPrivacy: limit each process to the data it has access permissionFairness: each user / process: should be limited to its "appropriate share" of system resources
- system protection features: guided by
- principle of need-to-know
- implement mechanisms to enforce: principle of least privilege
- minimum possible permission to do the job!
- computer systems contain object that must be protected from misuse
- hardware: memory, CPU time, IO devices
- software: files, programs, semaphores
- protection: internal problem